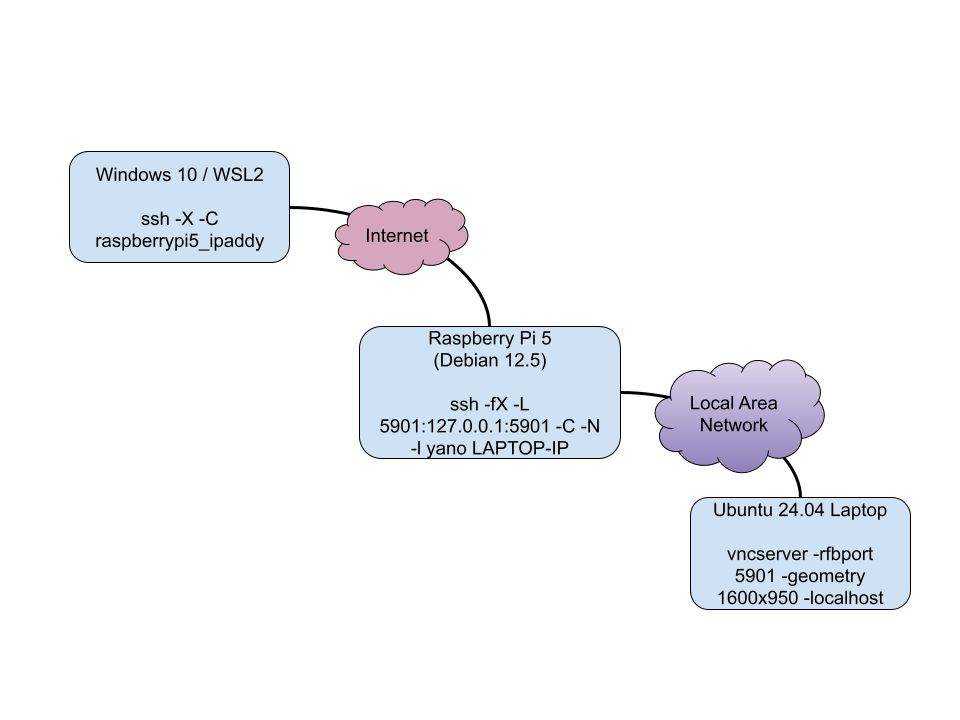
There have been situations where I've needed to access applications that run on my home network, or on Linux from a Windows machine. I found a way to make this work via vncviewer, vncserver, SSH, and X11 forwarding. This is likely a convoluted setup, but it works in a pinch for me.
To start off with, in this example, there are three servers/machines:
- an Ubuntu 24.04 laptop, let's call "machine #1"
- a Raspberry Pi 5, let's call "machine #2"
- a Windows 10 or 11 machine with Windows Subsystem for Linux 2 (WSL2) installed, let's call "machine #3"
For this set up, machine #1 and machine #2 are on the same local area network (LAN), however, machine #3 is located across the Internet.
The setup steps for this involved going to the machine you want to host the vncserver instance. This will be the machine that will load the applications in to memory. In my example, that is machine #3.
- On machine #3 (the machine I want vncserver on), I run
vncserver -rfbport 5901 -geometry 1600x950 -localhost
This makes vncserver only listen on localhost, so we can only access it locally which we will do via SSH.
- Next, go to machine #2 (the middle server), and run
ssh -fX -L 5901:127.0.0.1:5901 -C -N -l USER 192.168.1.101
Replace "user" with your username on machine #3 and the IP address with the IP of machine #3 in this case. This will open up port 5901 on localhost on machine #2, so any application that tries to access 5901 on machine #2 will access port 5901 on machine #3.
- Now, go to machine #1 and SSH in to machine #2 via,
ssh -X -C raspberrypi5_ipaddy
This will enable X11 forwarding with compression. Now, if you run vncviewer & on machine #2 while SSH'ed in from machine #1, you should get a GUI popup of vncviewer asking you to connect. In it, you will input 127.0.0.1:5901 because you want to connect to 5901 on the localhost of machine #2, which then connects to 5901 on machine #3 via the SSH tunnel.
Here is an overview picture of the pre-setup:
For added security, it is good to set up everything with SSH keys only, instead of SSH passwords.
Additionally, if you need to or want to (for whatever reason) you can add more "middle" machines running the command that is running on machine #2. SSH tunnels can be daisy chained. This can be helpful if you are on a restrictive network, like Wi-Fi at a hotel.

